Overview of Jasper Server Authentication & Authorization
In Jaspersoft Reports Server, access control is determined by two separate mechanisms, authentication and authorization.
- Authentication is the process of verifying user credentials to give access to the server.
- Authorization is the process of checking permissions granted to users and roles to access resources within the server.
Make data easy with Helical Insight.
Helical Insight is the world’s best open source business intelligence tool.
Authentication
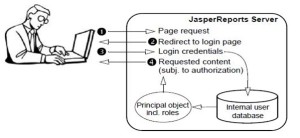
Authentication is the verification of a user’s identity to allow access to JasperReports Server. By default, anonymous access is disabled, and all users must present valid credentials to log in: a user ID, a password, and in certain cases an organization ID. Authentication is more than gathering the user credentials, it is a process that ensures that every page is secure, either viewed by a verified user or denied access until valid credentials are provided.
Jasper server supports following two types of authentication mechanisms:-
Internal Authentication (Default ):- DB based
External Authentication:- process of gathering and verifying user credentials through a third-party application; for example:-
- LDAP –
Lightweight Directory Access Protocol (LDAP) is one of the most popular architectures for enterprise directories. By centralizing all user management in an LDAP directory, applications across the enterprise can share the same user database, and administrators do not need to duplicate user accounts in every application. LDAP authentication does not provide single sign-on (SSO) functionality.
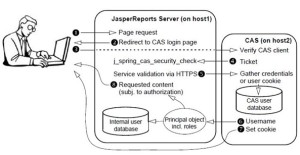
- CAS –
Central Authentication Service (CAS) is an open source, Java-based authentication server that includes a mechanism for single sign-on (SSO) across web applications, including those running on different application servers. When a user requests a page from a CAS-enabled web application, the application redirects the user to the CAS server login page. Thereafter, logged-in users can navigate between all participating applications without needing to log in again. Each application communicates with the CAS server in the background to verify that the user is valid before providing access to its resources.
Authentication happens only once at the beginning of the user’s session. After a user is authenticated, the user’s session is represented by an in-memory instance referred to as the principal object. The existence of the principal object determines that the user is logged on, and the user can access pages throughout the application. The principal object also stores the roles and organization ID of the user, which are required for authorization within JasperReports Server.
Authorization
Authorization is the verification of a user’s roles and organization ID to access features of the server, resources in the repository, and, in some cases, data. For every page that the user requests, the server determines which menu items, resources, and report contents the user can access, based on the principal object. Authorization happens every time a user accesses a resource.
In the JasperReports Server architecture, which is based on the Spring Framework and spring security authorization is always performed by internal mechanisms. Part of configuring external authentication is to define a mapping of external roles and organization IDs into the principal object so that authorization can proceed internally.
Authorization mechanism:-
- In JasperReports Server, all resources are stored in the repository in a hierarchical structure of folders.
- Each resource in the repository has a set of permissions explicitly granting certain kinds of access. Folders also have permissions, and all contents of a folder inherit these permissions if they do not explicitly define their own. Often, many resources need the same permissions, and therefore it is easier to manage permissions on folders.
- Permissions can grant access to users or to roles. Roles are groups of users created for the purpose of simplifying authorization. Often, it is easier to manage permissions for groups of users, and then manage role membership separately. However, if necessary, permissions can be granted to specific users.
– By Archana Verma

Best Open Source Business Intelligence Software Helical Insight is Here


Great post, Archana!
A few comments…
JasperReports Server does provide out of the box configurations that can be installed for LDAP/Active Directory and CAS. These configurations are based on a set of APIs within Jaspersoft that are used to integrate with a wide variety of authentication mechanisms – open source ones like Shibboleth, commercial platforms like Tivoli, and custom authentication/authorization schemes. This is all based on Spring Security.
There is the Jaspersoft Authentication Cookbook at http://community.jaspersoft.com/documentation that outlines all these APIs.