For data confidentiality and Data security purpose we can use the data in many places by encrypting it. Hereby using a java code we can get the encrypted data.
For Example, if we want to request a server to log in the user by sending a URL contains the user login details, here we can secure the user details by encrypting them and send via URL. There are so many algorithm’s and modes to encrypt the data. In my blog, I have used AES/ECB algorithm to generate the encrypted token.
Token Format
|u=< username >|p=|exp=< timestamp >
Token comprises of 3 parts separated by a “|” (pipe separator).
| Part of Token | Description/Format | Mandatory? | Example |
| Password | Password to be used for login | Yes | p=kasoji |
| username | Username to be used for login | Yes | U=prashanth |
| exp | Time-stamp with time zone
Format string YYYYMMDD HH:mm: ss Z
This is to make the token secure, so that same will not be usable after the expiry time is past. Not giving an expiry time will make the token never expiring and the same token can be used for the user indefinitely(this is not recommended).
|
No | exp=28-09-2018 04:06:00 |
Token Encryption
Token generated in the given format, has to be encrypted to make it secure.
Chosen Encryption Algorithm details:
- Algorithm – AES
- Mode – ECB
- Padding – PKCS5Padding
- Secret Key – XXXXXXX
- Encrypted token is Base64 URL Safe encoded
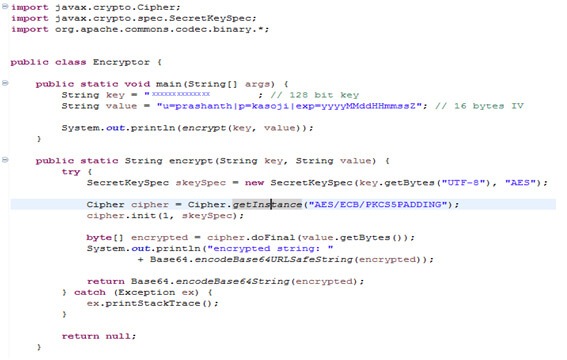
Encryption logic used (java code)
Token Samples for Testing
Below are few tokens and its encrypted form (using the shared secret key).
| Token | Encrypted token |
| u=prashanth | 7FZMAukMtsa_VOPiK9JbdQ |
| u=prashanth|p=kasoji | GVMypDdXCpP8Evy4ZGSrMqfPa_ulBGbrf4XIRUSGry4 |
| u=prashanth|p=kasoji|exp=28-09-2018 04:06:00 | GVMypDdXCpP8Evy4ZGSrMnN5l2WfJZ0xFtPdFBINFKnSNPk0K0AinND77ZagsTK3 |

Best Open Source Business Intelligence Software Helical Insight is Here

A Business Intelligence Framework
If you have any queries please get us at support@helicaltech.com
Thank You
Prashanth Kasoji
Helical IT Solutions Pvt Ltd