Domain Security in a Jasper Reports Server’s Multi-tenant Environment
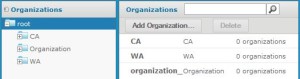
Create two tenants/organizations CA & WA
1. Log on Jasper report’s server as superuser.
2. Navigate to Manage > Organizations.
3. Click on ‘Add Organization’ button.
4. Enter valid organization name and id
Make data easy with Helical Insight.
Helical Insight is the world’s best open source business intelligence tool.
- CA as Organization Name (you can give ‘California’ as Organization Name)
- CA as Organization ID
Click on Add Organization button.
5. Repeat step 3 to4 to add ‘WA’ as another Organization.
At the end of step 5, two organizations are added to root as shown below:
Create two users CA_Manager & WA_Manager
1. Navigate to Manage > Users
2. Select CA organization from left panel.
3. Click on Add User button.
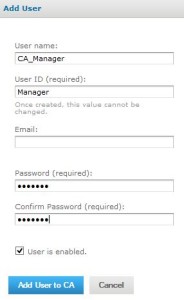
4. Enter details as shown in the figure below
User name: CA_Manager
User ID: Manager
Password: Manager
5. Click on ‘Add User to CA’ button.The user CA_Manager is now added to CA Organization.
6. Assign ROLE_SUPERMART_MANAGER to CA_Manager
7. Again click on Add User button to add another user.
8. Enter following details
User name: WA_Manager
User ID: Manager
Password: Manager
9. Click on ‘Add User to WA’ button.The user WA_Manager is now added to WA Organization.
10.Assign ROLE_SUPERMART_MANAGER to WA_Manager
Make data easy with Helical Insight.
Helical Insight is the world’s best open source business intelligence tool.
We have added two users CA_Manager & WA_Manager to CA & WA organizations respectively. See figure given below:
Implementing row level & column level security in Domain
Initial setup
For demo I’m using Supermart Domain which is already in Jasper Report’s server.
- Log on jasper report’s server as superuser.
- Copy ‘Analysis Components’ & ‘Domains’ folders and Paste them in CA &WA organizations.
- Make sure that in CA, the Supermart Domain in Domains folder should use ‘/organizations/CA/analysis/datasources/FoodmartDataSourceJNDI’ as datasource.
- Similarly in WA, Supermart Domain in Domains folder should use ‘/organizations/WA/analysis/datasources/FoodmartDataSourceJNDI’ as datasource.
- Set appropriate permissions for ROLE_SUPERMART_MANAGER in CA & WA organizations so that the user that belongs to CA & WA can access Supermart Domain.
Editing domain security file
- Log on jasper report’s server as superuser.
- Navigate to ‘/organizations/CA/Domains/supermartDomain’ in repository.
- Edit Supermart domain.
- Change security file with the updated domain security file. The contentof the file is given below. please, check the comments to understand how row level and column level security are implemented.
<securityDefinition xmlns="http://www.jaspersoft.com/2007/SL/XMLSchema" version="1.0" itemGroupDefaultAccess="granted"> <!-- For multi-tenancy demo. Assumes state abbreviations are used for the Organization ID (tenantId). Examples: Organization Names : CA, WA Organization IDs (tenantId) : CA, WA (tenantId maps to the values held in store_state) --> <!-- Row level grants --> <resourceAccessGrants> <resourceAccessGrantList id="sales_join_resource_access_grant" label="aLabel" resourceId="sales_join"> <resourceAccessGrants> <resourceAccessGrant id="sales_join_ROLE_SUPERMART_TENANTID_row_grant"> <principalExpression>authentication.principal.tenantId != null</principalExpression> <filterExpression>store1.store_state in (groovy('authentication.principal.tenantId.toUpperCase()'))</filterExpression> </resourceAccessGrant> </resourceAccessGrants> </resourceAccessGrantList> </resourceAccessGrants> <!-- Column level grants --> <!--Only ROLE_ADMINISTRATOR & ROLE_HR can access salary field--> <itemGroupAccessGrants> <itemGroupAccessGrantList id="restrictedHR__salary" label="aLabel" itemGroupId="salary" defaultAccess="denied"> <itemGroupAccessGrants> <itemGroupAccessGrant id="restrictedHR__salary__grant1" access="granted"> <principalExpression>authentication.getPrincipal().getRoles().any{ it.getRoleName() in ['ROLE_ADMINISTRATOR','ROLE_HR'] }</principalExpression> </itemGroupAccessGrant> </itemGroupAccessGrants> </itemGroupAccessGrantList> <!--ROLE_SUPERMART_MANAGER can partially access 'Employee Private' item group. That means it can access 'Min Scale' & 'Max Scale' but can not access 'Salary' from the item group. Where as, ROLE_ADMINISTRATOR & ROLE_HR can completely access 'Employee Private' item group --> <itemGroupAccessGrantList id="restrictedHR__employee__employee_private" label="aLabel" itemGroupId="employee__employee_private" defaultAccess="denied"> <itemGroupAccessGrants> <itemGroupAccessGrant id="restrictedHR__employee__employee_private__grant1" access="granted"> <principalExpression>authentication.getPrincipal().getRoles().any{ it.getRoleName() in ['ROLE_SUPERMART_MANAGER'] }</principalExpression> <itemAccessGrantList id="restrictedHR__employee__employee_private__grant1__items" defaultAccess="denied"> <itemAccessGrants> <itemAccessGrant id="restrictedHR__employee__employee_private__grant1__items__grant1" itemId="employee__employee_private__min_scale" access="granted" /> <itemAccessGrant id="restrictedHR__employee__employee_private__grant1__items__grant2" itemId="employee__employee_private__max_scale" access="granted" /> </itemAccessGrants> </itemAccessGrantList> </itemGroupAccessGrant> <itemGroupAccessGrant id="restrictedHR__employee_private__grant1" access="granted"> <principalExpression>authentication.getPrincipal().getRoles().any{ it.getRoleName() in ['ROLE_ADMINISTRATOR','ROLE_HR'] }</principalExpression> </itemGroupAccessGrant> </itemGroupAccessGrants> </itemGroupAccessGrantList> </itemGroupAccessGrants> </securityDefinition>
5. Click on submit button to save the changes.
Testing
Row Level Security
- On logging in as a jasperadmin you will be able to data of all states data from Sales dataset(as shown in the figure below) because there is no row level restriction for ROLE_ADMINISTRATOR.
- Logging in as Manager in CA organization you’ll be only able to access data which belongs to CA State.
- Logging in as Manager in WA organization you’ll be only able to access data which belongs to WA State.
Column Level Security
Make data easy with Helical Insight.
Helical Insight is the world’s best open source business intelligence tool.
- Jasperadmin will be able to access all fields/columns in Employees dataset because there is no column level restriction for ROLE_ADMINISTRATOR.
- Only jasperadmin can access salary field. CA_Manager & WA_Manager cannot access Salary column.
- CA_Manager & WA_Manager can partially access ‘Employee Private’ column group. That means they can access ‘Min Scale’ & ‘Max Scale’ columns but cannot access ‘Salary’ column from the group. Whereas, jasperadmin has complete access to ‘Employee Private’ column group.
This is how row level & column level security can be implemented in domain in a multi-tenant environment.
-By
Archana Verma

Best Open Source Business Intelligence Software Helical Insight is Here